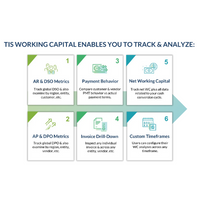
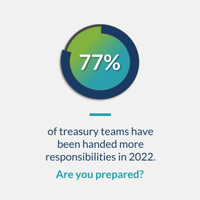
https://treasuryxl.com/wp-content/uploads/2024/12/FIS-BLOGS-featured-4.png
200
200
treasuryXL
https://treasuryxl.com/wp-content/uploads/2018/07/treasuryXL-logo-300x56.png
treasuryXL2025-01-08 07:00:412025-01-07 10:39:33Unlocking Value: How TMS Delivers Measurable ROI for Corporate Treasury
https://treasuryxl.com/wp-content/uploads/2024/12/FIS-BLOGS-featured-4.png
200
200
treasuryXL
https://treasuryxl.com/wp-content/uploads/2018/07/treasuryXL-logo-300x56.png
treasuryXL2025-01-08 07:00:412025-01-07 10:39:33Unlocking Value: How TMS Delivers Measurable ROI for Corporate TreasuryFor corporate treasury, fraud and cybersecurity are direct threats to the company’s most liquid assets. The function’s access to payment systems and sensitive financial data makes it a prime target. Protection is not an IT issue alone; it is a core operational responsibility of the treasury department.
For corporate treasury, fraud and cybersecurity are direct threats to the company’s most liquid assets. The function’s access to payment systems and sensitive financial data makes it a prime target. Protection is not an IT issue alone; it is a core operational responsibility of the treasury department.
Primary Threats Targeting Treasury
Treasury faces specific, high-impact attack vectors:
-
Business Email Compromise (BEC / “CEO Fraud”): The most common and damaging threat. Criminals impersonate executives or trusted partners via email to authorize fraudulent wire transfers.
-
Payment Process Fraud: This includes internal fraud through the manipulation of payment files or vendor master data to divert funds, and external fraud through forged checks or intercepted electronic payments.
-
System Takeover: Attackers gain access to treasury’s bank portals or Treasury Management System (TMS) through stolen credentials or malware to initiate payments directly.
-
Data Breach & Espionage: Theft of confidential financial data, such as merger plans or bank account details, used for competitive advantage or to enable further fraud.
A Practical Defense Framework: The Three Lines of Control
Effective protection requires layered defenses across people, processes, and technology.
| Defense Layer | Key Treasury Controls & Actions |
|---|---|
| Process & Authorization | • Strict Payment Verification: Enforce a mandatory, out-of-band confirmation process (e.g., phone call-back) for all new or amended vendor details and high-value transactions. • Segregation of Duties: Ensure no single individual can initiate, approve, and reconcile payments. Separate TMS/Bank portal access rights accordingly. • Regular Audits: Conduct surprise audits of payment logs and vendor master files. |
| Technological Safeguards | • Multi-Factor Authentication (MFA): Require MFA for all access to bank portals, the TMS, and email systems. This is non-negotiable. • Payment Positive Pay: Use bank services that match check/ACH details against an issued file before clearing. • System Logging & Monitoring: Implement alerts for unusual activity (e.g., login from a new device, large payment batch creation). |
| Human Vigilance | • Targeted Training: Conduct regular, simulated phishing exercises and training focused on recognizing payment-related scams. • Clear Reporting Channels: Establish and communicate a simple, non-punitive process for employees to report suspicious emails or activity. • Vendor Due Diligence: Implement formal verification procedures for onboarding new vendors, especially those requesting electronic payments. |
Essential Actions for Incident Response
A prepared treasury department has a plan that is rehearsed:
-
Immediate Containment: Designated staff must know how to immediately contact banks to stop payments and freeze compromised accounts.
-
Preserve Evidence: Isolate affected systems without shutting them down to preserve forensic data. Document all steps taken.
-
Activate the Team: Have clear contacts for internal legal, communications, and external cybersecurity forensic experts.
-
Communicate with Precision: Follow a pre-defined protocol to inform senior management, law enforcement, and insurers without causing unnecessary public alarm.
In practice, treasury’s role is to build a culture of controlled skepticism. Every payment instruction, especially those requesting urgency or secrecy, must be verified. By embedding these controls into daily routines, treasury moves from being a vulnerable target to a secure guardian of corporate value.
Treasury faces specific, high-impact attack vectors:
-
Business Email Compromise (BEC / “CEO Fraud”): The most common and damaging threat. Criminals impersonate executives or trusted partners via email to authorize fraudulent wire transfers.
-
Payment Process Fraud: This includes internal fraud through the manipulation of payment files or vendor master data to divert funds, and external fraud through forged checks or intercepted electronic payments.
-
System Takeover: Attackers gain access to treasury’s bank portals or Treasury Management System (TMS) through stolen credentials or malware to initiate payments directly.
-
Data Breach & Espionage: Theft of confidential financial data, such as merger plans or bank account details, used for competitive advantage or to enable further fraud.
A Practical Defense Framework: The Three Lines of Control
Effective protection requires layered defenses across people, processes, and technology.
| Defense Layer | Key Treasury Controls & Actions |
|---|---|
| Process & Authorization | • Strict Payment Verification: Enforce a mandatory, out-of-band confirmation process (e.g., phone call-back) for all new or amended vendor details and high-value transactions. • Segregation of Duties: Ensure no single individual can initiate, approve, and reconcile payments. Separate TMS/Bank portal access rights accordingly. • Regular Audits: Conduct surprise audits of payment logs and vendor master files. |
| Technological Safeguards | • Multi-Factor Authentication (MFA): Require MFA for all access to bank portals, the TMS, and email systems. This is non-negotiable. • Payment Positive Pay: Use bank services that match check/ACH details against an issued file before clearing. • System Logging & Monitoring: Implement alerts for unusual activity (e.g., login from a new device, large payment batch creation). |
| Human Vigilance | • Targeted Training: Conduct regular, simulated phishing exercises and training focused on recognizing payment-related scams. • Clear Reporting Channels: Establish and communicate a simple, non-punitive process for employees to report suspicious emails or activity. • Vendor Due Diligence: Implement formal verification procedures for onboarding new vendors, especially those requesting electronic payments. |
Essential Actions for Incident Response
A prepared treasury department has a plan that is rehearsed:
-
Immediate Containment: Designated staff must know how to immediately contact banks to stop payments and freeze compromised accounts.
-
Preserve Evidence: Isolate affected systems without shutting them down to preserve forensic data. Document all steps taken.
-
Activate the Team: Have clear contacts for internal legal, communications, and external cybersecurity forensic experts.
-
Communicate with Precision: Follow a pre-defined protocol to inform senior management, law enforcement, and insurers without causing unnecessary public alarm.
In practice, treasury’s role is to build a culture of controlled skepticism. Every payment instruction, especially those requesting urgency or secrecy, must be verified. By embedding these controls into daily routines, treasury moves from being a vulnerable target to a secure guardian of corporate value.