Update Digital Finance Summit 2020
| 02-12-2020 | François de Witte | treasuryXL |
After having worked for more than 30 years in banking, François launched his own consultancy activity, FDW Consult, specialized in finance and treasury consulting. From 2014 to 2016, he was also Solution Partner Treasury & Finance at USG Professionals. Since then he took up several assignments, including one in the automotive sector with Ginion Group and with Ibanity, part of Isabel Group in the area of PSD2 and open banking. He currently is Senior Project Manager Treasury at Gaming1 (part of Ardent-Group). 
Introduction
For the 5th year, Fintech Belgium organized its annual seminar, the Digital Finance Summit, this year with as main theme “The World After”.
Due to the current sanitary situation, this year’s edition went entirely ONLINE! It was attended by over 400 persons. There were also over 230 virtual stands of exhibitors; The organization was seamless. I perceived a participant experience which was not that far away from a physical gathering.
Some messages
Main Stage Sessions
During the general sessions, the main message was Digital becoming the new normal. Xavier Corman, Board Member of Fintech Belgium stated: “The Covid Crisis has also brought good thing. Years worth of Digital transformation.”.
Despite the virtual exchanges, which following on the COVID19 crisis, increased dramatically, in a digital worlds, People and trust become more important. We got also interesting testimonies of banks moving to disruptive models, such as Aion (e-bank providing full set of services for a fixed subscription fee and KBC (using AI models to improve its services in the insurance).
There is a large need for digital identity, like e.g. ITSME in Belgium, but more importantly of the interoperability of the digital identity solutions. Prof Bruno Colmant • highlighted that the creation of Digital currencies represent a new paradigm and a tectonic revolution in the monetary landscape.
Evolution in the cards Landscape
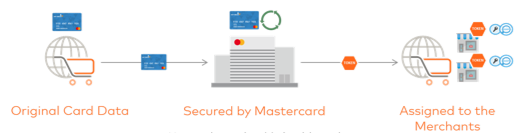
Within the cards busine, the tokenization of cards is increasing, reducing the friction, whilst keeping the security.
Tokenization is the process of protecting sensitive data by replacing it with an algorithmically generated number called a token. Often times tokenization is used to prevent credit card fraud. In credit card tokenization, the customer’s primary account number (PAN) is replaced with a series of randomly generated numbers, which ares called the “token.” These tokens can then be passed through the internet needed to process the payment without actual bank details being exposed. The actual bank account or credit card number is held safe in a secure token vault.
Evolution in the payments world
Following a three-month public consultation, the EPC (European Payment Council) has published on 30/11/2020 the first version of the SEPA Request-To-Pay (RTP) scheme rulebook. The Request to Pay (RtP) is an umbrella term for several scenarios in which a payee takes the initiative to request a specific payment from the payer.
The scheme covers the set of operating rules and technical elements (including messages) that allow a Payee to request the initiation of a payment from a Payer in a wide range of physical or online use cases. The scheme can be considered as a complement to the payment flow because it supports the end-to-end process and lies between an underlying commercial transaction and the payment itself. An RTP as such can be seen as an enabler for digital payments.
The first release of the SEPA RTP scheme is scheduled to go live on 15/6/2021. The SEPA RTP scheme, combined with the SEPA Instant Credit Transfer could be a challenger for card payments, being much cheaper for the merchants. It might take some time to take off.
Conclusion
This conference was a good forum to get an insight in the Belgian FinTech market. I saw a lot of interesting initiatives and consider that Fintech will bring a lot of added value in the payments and corporate treasury landscape.
If you want to learn more on this topic, I invite you to attend the one day training session, which I animate on the topic on 16/12/2020 “PSD2 & Open banking: impact on the financial ecosystem and new challenges”

François de Witte
Founder & Senior Consultant at FDW Consult
Managing Director and CFO at SafeTrade Holding S.A.
treasuryXL ambassador